 Exploite Access Interface
Exploite Access Interface
The IC attacker could be also applied to the device communication protocol in order to find any hidden functions embedded by the software developer for testing and upgrade purposes. Chip manufacturers very often embed hardware test interfaces for postproduction testing of their semiconductor devices. If the security protection for these interfaces is not properly designed, the attacker can exploit it to get access to the on-chip memory. In smartcards such test interfaces are normally located outside the chip circuit and physically removed after the test operation, eliminating any possibility of use by outsiders.
 Recover Protected Microcontroller ATmega1284PA Heximal
Recover Protected Microcontroller ATmega1284PA Heximal
We can recover protected microcontroller ATMEGA1284PA heximal, please view the protected microcontroller ATMEGA1284PA features for your reference:
A normal conversion takes 13 ADC clock cycles. In certain situations, the ADC needs more clock cycles to perform initialization and minimize offset errors. These extended conversions take 25 ADC clock cycles and occur as the first conversion after one of the following events when recover protected microcontroller heximal:
the ADC is switched on (ADEN in ADCSR is set) the voltage reference source is changed (the REFS1..0 bits in ADMUX change value) a differential channel is selected (MUX2 in ADMUX is “1”) if recover protected microcontroller heximal.
Note that subsequent conversions on the same channel are not extended conversions.
The actual sample-and-hold takes place 1.5 ADC clock cycles after the start of a normal conversion and 13.5 ADC clock cycles after the start of an extended conversion. When a conversion is complete, the result is written to the ADC data registers, and ADIF is set before recover protected microcontroller heximal.
In Single Conversion mode, ADSC is cleared simultaneously. The software may then set ADSC again, and a new conversion will be initiated on the first rising ADC clock edge after recover protected microcontroller heximal.
In Free Running mode, a new conversion will be started immediately after the conversion completes while ADSC remains high. Using Free Running mode and an ADC clock frequency of 200 kHz gives the lowest conversion time, 65 µs, equivalent to 15 kSPS when recover protected microcontroller heximal.
For a summary of conversion times, see Table 18. The ADC features a noise canceler that enables conversion during ADC Noise Reduction mode (see “Sleep Modes” on page 23) to reduce noise induced from the CPU core and other I/O peripherals if recover protected microcontroller heximal.
If other I/O peripherals must be active during conversion, this mode works equivalently for Idle mode. To make use of this feature, the following procedure should be used before recover protected microcontroller heximal:
1. Make sure that the ADC is enabled and is not busy converting. Single Conversion mode must be selected and the ADC conversion complete interrupt must be enabled.
ADEN = 1
ADSC = 0
ADFR = 0
ADIE = 1
2. Enter ADC Noise Reduction mode (or Idle mode). The ADC will start a conversion once the CPU has been halted.
3. If no other interrupts occur before the ADC conversion completes, the ADC interrupt will wake up the protected microcontroller and execute the ADC conversion complete interrupt routine after recover protected microcontroller heximal.
 Brute Force Eeprom Attack
Brute Force Eeprom Attack
Another possible brute force eeprom attack, applicable to many semiconductor chips, is applying an external high voltage signal (normally twice the power supply) to the chip’s eeprom pins to find out whether one of them has any transaction like entering into a factory test or programming mode. In fact, such pins can be easily found with a digital multimeter because they do not have a protection diode to the power supply line. Once sensitivity to a high voltage is found for any pin, the eeprom attacker can try a systematic search on possible combinations of logic signals applied to other pins to figure out which of them are used for the test/programming mode and exploit this opportunity.
 Reverse Engineering Microprocessor ATmega1284PV Embedded Firmware
Reverse Engineering Microprocessor ATmega1284PV Embedded Firmware
We can reverse engineering Microprocessor ATMEGA1284PV embedded firmware, please view the Microprocessor ATMEGA1284PV features for your reference:
These bits select the voltage reference for the ADC, as shown in Table 19. If these bits are changed during a conversion, the change will not go into effect until this conversion is complete (ADIF in ADCSR is set).
Whenever these bits are changed, the next conversion will take 25 ADC clock cycles. If active channels are used, using AVCC or an external AREF higher than (AVCC – 1V) is not recommended, as this will affect ADC accuracy.
The internal voltage reference options may not be used if an external reference voltage is being applied to the AREF pin. The ADLAR bit affects the presentation of the ADC conversion result in the ADC Data Register.
If ADLAR is cleared, the result is right-adjusted. If ADLAR is set, the result is left-adjusted. Changing the ADLAR bit will affect the ADC Data Register immediately, regardless of any ongoing conversions after reverse engineering Microprocessor ATMEGA1284PV embedded firmware.
For a complete description of this bit, see “The ADC Data Register. The value of these bits selects which analog input is connected to the ADC. In case of differential input (PB3 – PB4), gain selection is also made with these bits. Selecting PB3 as both inputs to the differential gain stage enables offset measurements.
Refer to Table 20 for details. If these bits are changed during a conversion, the change will not go into effect until this conversion is complete (ADIF in ADCSR is set). Writing a logical “1” to this bit enables the ADC. By clearing this bit to zero, the ADC is turned off if reverse engineering Microprocessor ATMEGA1284PV embedded firmware.
Turning the ADC off while a conversion is in progress will terminate this conversion. In Single Conversion mode, a logical “1” must be written to this bit to start each conversion. In Free Running mode, a logical “1” must be written to this bit to start the first conversion.
When the conversion completes, ADSC returns to zero in Single Conversion mode and stays high in Free Running mode. Writing a “0” to this bit has no effect. When this bit is set (one), the ADC operates in Free Running mode. In this mode, the ADC samples and updates the data registers continuously after reverse engineering Microprocessor ATMEGA1284PV embedded firmware.
Clearing this bit (zero) will terminate Free Running mode. If active channels are used (MUX2 in ADMUX set), the channel must be selected before entering Free Running mode. Selecting an active channel after entering Free Running mode may result in undefined operation from the ADC when reverse engineering Microcontroller.
 Brute Force Chip Break Application
Brute Force Chip Break Application
Brute force chip break can be also applied to a hardware design implemented into an ASIC or a CPLD. In this case the chip breaker tries to apply all possible logic combinations to the input of the device while observing all its outputs.
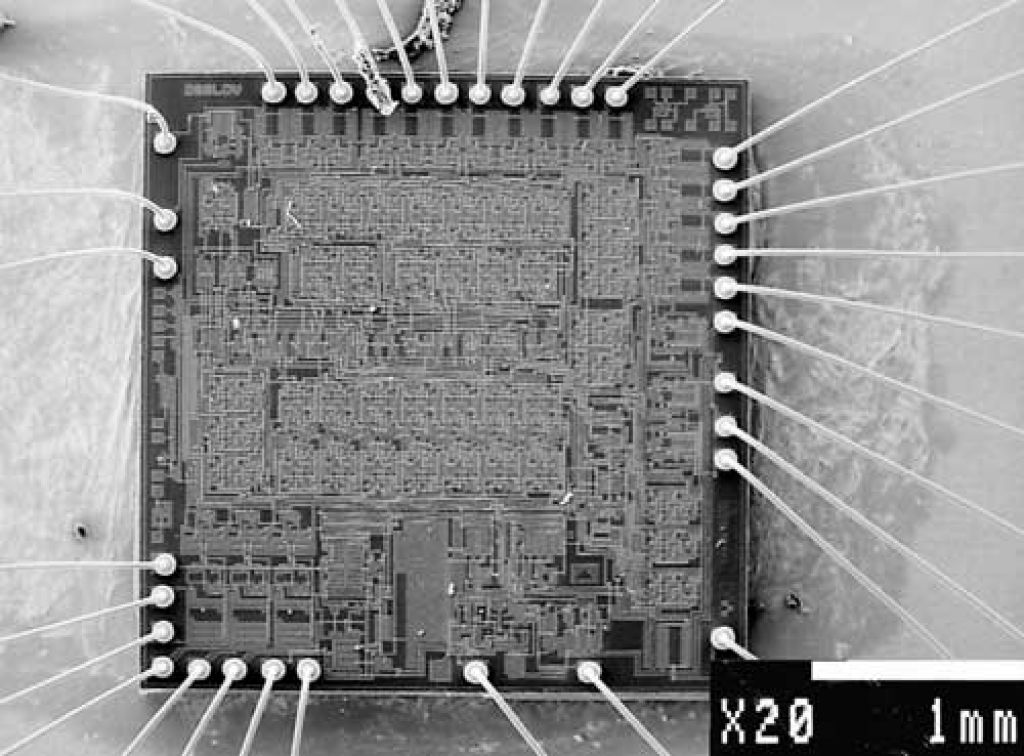
That kind of microcontroller breaking could be also called black-box analysis because the MCU cracker does not have to know anything about the design of the device under test.
He only tries to understand the function of the device by trying all possible combinations of signals. This approach works well only for relatively small logic devices. Another problem the MCU reading process will face is that designs implemented in CPLDs or ASICs have flip-flops, so the output will probably be function of both the previous state and the input.
But the search space can be significantly reduced if the signals are observed and analysed beforehand. For example, clock inputs, data buses and some control signals could be easily identified, significantly reducing the area of search.
 Dump Microcontroller ATMEGA1284V Source Code
Dump Microcontroller ATMEGA1284V Source Code
We can dump microcontroller ATMEGA1284V source code, please view the microcontroller ATMEGA1284V features for your reference:
This bit is set (one) when an ADC conversion completes and the data registers are updated. The ADC Conversion Complete Interrupt is executed if the ADIE bit and the I-bit in SREG are set (one).
ADIF is cleared by hardware when executing the corresponding interrupt handling vector. Alternatively, ADIF is cleared by writing a logical “1” to the flag.
Beware that if doing a read-modify-write on ADCSR, a pending interrupt can be disabled. This also applies if the SBI and CBI instructions are used before Dump Microcontroller ATMEGA1284V Source Code.
· Bit 3 – ADIE: ADC Interrupt Enable
When this bit is set (one) and the I-bit in SREG is set (one), the ADC Conversion Complete Interrupt is activated.
· Bits 2..0 – ADPS2..ADPS0: ADC Prescaler Select Bits
These bits determine the division factor between the CK frequency and the input clock to the ADC. When an ADC conversion is complete, the result is found in these two registers.
When ADCL is read, the ADC Data Register is not updated until ADCH is read. If the result is left adjusted and no more than 8-bit precision is required, it is sufficient to read ADCH.
Otherwise, ADCL must be read first, then ADCH. The ADLAR bit in ADMUX affects the way the result is read from the registers. If ADLAR is set, the result is left-adjusted if Dump Microcontroller ATMEGA1284V Source Code.
If ADLAR is cleared (default), the result is right-adjusted.
· ADC9..0: ADC Conversion Result
These bits represent the result from the conversion. For the differential channel, this is the value after gain adjustment, as indicated in Table 20 on page 47. For single-ended conversion, or if ADLAR or SIGN is zero, $000 represents ground and $3FF represents the selected reference voltage minus one LSB.
Since change of analog channel always is delayed until a conversion is finished, the Free Running mode can be used to scan multiple channels without interrupting the converter.
Typically, the ADC Conversion Complete Interrupt will be used to perform the channel shift. However, the user should take the following fact into consideration:
The interrupt triggers once the result is ready to be read. In Free Running mode, the next conversion will start immediately when the interrupt triggers. If ADMUX is changed after the interrupt triggers, the next conversion has already started, and the old setting is used if Dump Microcontroller ATMEGA1284V Source Code.
 Brute Force IC Break Example
Brute Force IC Break Example
Brute Force IC Break is a process through which the inner circuitry pattern of MCU will be changed include decapsulation, focus ion beam and laser cut ways;
Brute force IC break’s one good example could be the password protection scheme used in microcontrollers, such as the Texas Instruments MSP430 family. The password itself is 32 bytes (256 bits) long which is more than enough to withstand direct brute force MCU breaking methods.
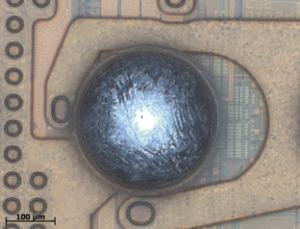
Brute Force IC Break is a process through which the inner circuitry pattern of MCU will be changed include decapsulation, focus ion beam and laser cut ways
But the password is allocated at the same memory addresses as the CPU interrupt vectors. That, firstly, reduces the area of search as the vectors always point to even addresses within memory. Secondly, when the software gets updated, only a small part of the password is changed because most of the interrupt subroutines pointed to by the vectors are very likely to stay at the same addresses.
As a result, if the IC code extractor knows one of the previous passwords he could easily do a systematic search and find the correct password in a reasonable time.
 Brute Force Chip Attack
Brute Force Chip Attack
Brute Force Chip Attack include invasive and semi-invasive microcontroller cracking, hardware attacking will be able to get access to embedded memory such as flash and eeprom memory, then readout firmware from Microprocessor memory;
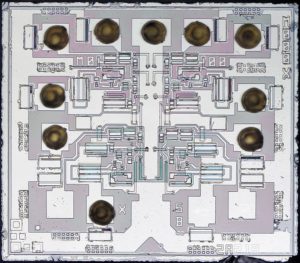
Brute Force Chip Attack include invasive and semi-invasive microcontroller cracking, hardware attacking will be able to get access to embedded memory such as flash and eeprom memory, then readout firmware from Microprocessor memory
MCU Attack has different meanings for cryptography and semiconductor hardware. In cryptography, a brute force chip attack would be defined as the methodical application of a large set of trials for a key to the system. This is usually done with a computer or an array of FPGAs delivering patterns at high speed and looking for success.
 Decrypt IC ATmega640P Secured Code
Decrypt IC ATmega640P Secured Code
We can decrypt IC ATMEGA640P secured code, please view the IC ATMEGA640P features for your reference:
Digital circuitry inside and outside the ATmega640P generates EMI, which might affect the accuracy of analog measurements. If conversion accuracy is critical, the noise level can be reduced by applying the following techniques:
1. The analog part of the ATmega640P and all analog components in the application should have a separate analog ground plane on the PCB. This ground plane is connected to the digital ground plane via a single point on the PCB.
2. Keep analog signal paths as short as possible. Make sure analog tracks run over the analog ground plane, and keep them well away from high-speed switching digital tracks before Decrypt IC ATmega640P Secured Code.
3. Use the ADC noise canceler function to reduce induced noise from the CPU.
4. If some Port B pins are used as digital outputs, it is essential that these do not switch while a conversion is in progress.
All AVR ports have true read-modify-write functionality when used as general digital I/O ports. This means that the direction of one port pin can be changed without unintentionally changing the direction of any other pin with the SBI and CBI instructions.
The same applies for changing drive value (if configured as output) or enabling/disabling of pull-up resistors (if configured as input). Port B is a 6-bit bi-directional I/O port when Decrypt IC ATmega640P Secured Code.
Three data memory address locations are allocated for Port B, one each for the Data Register – PORTB, $18, Data Direction Register – DDRB, $17, and the Port B Input Pins – PINB, $16. The Port B Input Pins address is read-only, while the Data Register and the Data Direction Register are read/write.
Ports PB5..0 have special functions as described in the section “Pin Descriptions” on page 4. If PB5 is not configured as external reset, it is input with no pull-up or as an open-drain output.
All I/O pins have individually selectable pull-ups, which can be over- ridden with pull-up disable. The Port B output buffers on PB0 to PB4 can sink 20 mA and thus drive LED displays directly before decrypt IC secured code.
PB5 can sink 12 mA. When pins PB0 to PB4 are used as inputs and are externally pulled low, they will source current (IIL) if the internal pull-ups are activated after BREAK IC.
 How to Prevent MCU Timing Attack
How to Prevent MCU Timing Attack
To prevent MCU timing attacks, the designer should carefully calculate the number of CPU cycles that take place when the password is compared and make sure they are the same for correct and incorrect passwords. For example, in the Motorola 68HC08 microcontrollers family the internal ROM bootloader allows access to the Flash memory only if the correct eight-byte password was entered first.
To achieve that, extra NOP commands were added to the program making the processing time equal for both correct and incorrect bytes of the password. That gives good protection against MCU timing attacks. Some microcontrollers have an internal RC generator mode of operation in which the CPU running frequency depends upon the power supply voltage and the die temperature which will greatly increase the difficulty of MCU cracking.
This makes timing analysis more difficult as the MCU attacker has to stabilize the device temperature and reduce any fluctuations and noise on the power supply line. Some smartcards have an internally randomised clock signal to make measurements of the time delays useless for the attack.