Archive for November, 2012
 modem- or network-card adapt to PC condition
modem- or network-card adapt to PC condition
Anyone who has ever tried to add a modem- or network-card to a PC knows that such an undertaking may produce unwanted results and can take more time than expected. To achieve cost savings from high volume production, the add-in board is designed to be logically compatible to a large variety of motherboards from various vendors. This flexibility makes it necessary to configure the board for its operating environment before it is ready to function. To perform the configuration one needs two pieces of information: sufficient knowledge of the system that the board is expected to reside in and knowledge of the board itself. Once the suitable settings are determined one needs to set jumpers or flip switches on the board. This completes the tricky part of the hardware installation.
 Dump Microcontroller ATMEGA128V Locked Code
Dump Microcontroller ATMEGA128V Locked Code
We can dump microcontroller ATMEGA128V locked code, please view the microcontroller ATMEGA128V features for your reference:
The ATMEGA128V provides the following standard features: 12K bytes of Downloadable locked code, 256 bytes of RAM, 32 I/O lines, programmable watchdog timer, two Data Pointers, three 16-bit timer/counters, a six-vector two-level interrupt architecture, a full duplex serial port, on-chip oscillator, and clock circuitry.
In addition, the ATMEGA128V is designed with static logic for operation down to zero frequency and supports two software selectable power saving modes. The Idle Mode stops the CPU while allowing the RAM, timer/counters, serial port, and interrupt system to continue functioning if Dump Microcontroller ATMEGA128V Locked Code.
The Power Down Mode saves the RAM contents but freezes the oscillator, disabling all other chip functions until the next interrupt or hardware reset.
The Downloadable locked code can be changed a single byte at a time and is accessible through the SPI serial interface. Holding RESET active forces the SPI bus into a serial programming interface and allows the program memory to be written to or read from unless Lock Bit 2 has been activated after Dump Microcontroller ATMEGA128V Locked Code.
Port 0 is an 8-bit open drain bidirectional I/O port. As an output port, each pin can sink eight TTL inputs. When 1s are written to port 0 pins, the pins can be used as high impedance inputs. Port 0 can also be configured to be the multiplexed low order address/data bus during accesses to external program and data memory. In this mode, P0 has internal pullups.
Port 0 also receives the code bytes during locked code programming and outputs the code bytes during program verification. External pullups are required during program verification before Dump Microcontroller ATMEGA128V Locked Code.
Port 1 is an 8-bit bidirectional I/O port with internal pullups. The Port 1 output buffers can sink/source four TTL inputs. When 1s are written to Port 1 pins, they are pulled high by the internal pullups and can be used as inputs. As inputs, Port 1 pins that are externally being pulled low will source current (IIL) because of the internal pullups.
Some Port 1 pins provide additional functions. P1.0 and P1.1 can be configured to be the timer/counter 2 external count input (P1.0/T2) and the timer/counter 2 trigger input (P1.1/T2EX), respectively after REVERSE ENGINEERING MICROCONTROLLER.
 Recover Locked Chip ATMEGA128PV Binary
Recover Locked Chip ATMEGA128PV Binary
We can recover locked chip ATMEGA128PV binary, please view the locked chip ATMEGA128PV features for your reference:
Port 1 also receives the low-order address bytes during Flash programming and verification.
Port 2
Port 2 is an 8-bit bidirectional I/O port with internal pullups. The Port 2 output buffers can sink/source four TTL inputs. When 1s are written to Port 2 pins, they are pulled high by the internal pullups and can be used as inputs when Recover Locked Chip ATMEGA128PV Binary.
As inputs, Port 2 pins that are externally being pulled low will source current (IIL) because of the internal pullups. Port 2 emits the high-order address byte during fetches from external program memory and during accesses to external data memory that use 16-bit addresses (MOVX @ DPTR).
In this application, Port 2 uses strong internal pullups when emitting 1s. During accesses to external data memory that use 8-bit addresses (MOVX @ RI), Port 2 emits the contents of the P2 Special Function Register.
Port 2 also receives the high-order address bits and some control signals during Flash programming and verification.
Port 3
Port 3 is an 8 bit bidirectional I/O port with internal pullups. The Port 3 output buffers can sink/source four TTL inputs. When 1s are written to Port 3 pins, they are pulled high by the internal pullups and can be used as inputs after Recover Locked Chip ATMEGA128PV Binary.
As inputs, Port 3 pins that are externally being pulled low will source current (IIL) because of the pullups. Port 3 also serves the functions of various special features of the AT89S53, as shown in the following table. Port 3 also receives some control signals for Flash programming and verification.
Reset input. A high on this pin for two machine cycles while the oscillator is running resets the device.
ALE/PROG
Address Latch Enable is an output pulse for latching the low byte of the address during accesses to external memory. This pin is also the program pulse input (PROG) during Flash programming.
In normal operation, ALE is emitted at a constant rate of 1/6 the oscillator frequency and may be used for external timing or clocking purposes. Note, however, that one ALE pulse is skipped during each access to external data memory before RECOVER MCU.
 Decrypt Locked MCU ATMEGA128V Embedded Firmware
Decrypt Locked MCU ATMEGA128V Embedded Firmware
We can decrypt locked MCU ATMEGA128V embedded firmware, please view the locked MCU ATMEGA128V features for your reference:
If desired, ALE operation can be disabled by setting bit 0 of SFR location 8EH. With the bit set, ALE is active only during a MOVX or MOVC instruction. Otherwise, the pin is weakly pulled high. Setting the ALE-disable bit has no effect if the microcontroller is in external execution mode.
Program Store Enable is the read strobe to external program memory. When the AT89S53 is executing embedded firmware from external program memory, PSEN is activated twice each machine cycle, except that two PSEN activations are skipped during each access to external data memory before Decrypt Locked MCU ATMEGA128V Embedded Firmware.
External Access Enable. EA must be strapped to GND in order to enable the device to fetch embedded firmware from external program memory locations starting at 0000H up to FFFFH. Note, however, that if lock bit 1 is programmed, EA will be internally latched on reset.
EA should be strapped to VCC for internal program executions. This pin also receives the 12-volt programming enable voltage (VPP) during Flash programming when 12-volt programming is selected.
A map of the on-chip memory area called the Special Function Register (SFR) space is shown in Table 1. Note that not all of the addresses are occupied, and unoccupied addresses may not be implemented on the chip when Decrypt Locked MCU ATMEGA128V Embedded Firmware.
Read accesses to these addresses will in general return random data, and write accesses will have an indeterminate effect. User software should not write 1s to these unlisted locations, since they may be used in future products to invoke new features. In that case, the reset or inactive values of the new bits will always be 0.
Timer 2 Registers Control and status bits are contained in registers T2CON (shown in Table 2) and T2MOD (shown in Table 9) for Timer 2. The register pair (RCAP2H, RCAP2L) are the Capture/Reload registers for Timer 2 in 16 bit capture mode or 16-bit auto-reload mode before Decrypt Locked MCU ATMEGA128V Embedded Firmware.
Watchdog Control Register The WCON register contains control bits for the Watchdog Timer (shown in Table 3). The DPS bit selects one of two DPTR registers available after BREAK IC.
 Decrypt Microprocessor ATMEGA169PA Code
Decrypt Microprocessor ATMEGA169PA Code
We can decrypt Microprocessor ATMEGA169PA code, please view the Microprocessor ATMEGA169PA features for your reference:
SPI Registers Control and status bits for the Serial Peripheral Interface are contained in registers SPCR (shown in Table 4) and SPSR (shown in Table 5). The SPI data bits are contained in the SPDR register.
Writing the SPI data register during serial data transfer sets the Write Collision bit, WCOL, in the SPSR register. The SPDR is double buffered for writing and the values in SPDR are not changed by Reset if decrypt Microprocessor code.
Interrupt Registers The global interrupt enable bit and the individual interrupt enable bits are in the IE register. In addition, the individual interrupt enable bit for the SPI is in the SPCR register. Two priorities can be set for each of the six interrupt sources in the IP register before Decrypt Microprocessor ATMEGA169PA Code.
Dual Data Pointer Registers To facilitate accessing external data memory, two banks of 16 bit Data Pointer Registers are provided: DP0 at SFR address locations 82H-83H and DP1 at 84H-85H. Bit DPS = 0 in SFR WCON selects DP0 and DPS = 1 selects DP1.
The user should always initalize the DPS bit to the appropriate value before accessing the respective Data Pointer register.
Power Off Flag The Power Off Flag (POF) is located at bit_4 (PCON.4) in the PCON SFR. POF is set to “1” during power up. It can be set and reset under software control and is not affected by RESET when Decrypt Microprocessor ATMEGA169PA Code.
The ATMEGA169PA implements 256 bytes of RAM. The upper 128 bytes of RAM occupy a parallel space to the Special Function Registers. That means the upper 128 bytes have the same addresses as the SFR space but are physically separate from SFR space.
When an instruction accesses an internal location above address 7FH, the address mode used in the instruction specifies whether the CPU accesses the upper 128 bytes of RAM or the SFR space. Instructions that use direct addressing access SFR space.
For example, the following direct addressing instruction accesses the SFR at location 0A0H (which is P2) after Decrypt Microprocessor ATMEGA169PA Code.
 Recover Microcontroller ATmega169PV Heximal
Recover Microcontroller ATmega169PV Heximal
We can recover Microcontroller ATmega169PV heximal, please view the Microcontroller ATmega169PV features for your reference:
Instructions that use indirect addressing access the upper 128 bytes of RAM. For example, the following indirect addressing instruction, where R0 contains 0A0H, accesses the data byte at address 0A0H, rather than P2 (whose address is 0A0H).
MOV @R0, #data Note that stack operations are examples of indirect addressing, so the upper 128 bytes of data RAM are available as stack space if Recover Microcontroller ATMEGA169PV Heximal.
The programmable Watchdog Timer (WDT) operates from an independent oscillator. The prescaler bits, PS0, PS1 and PS2 in SFR WCON are used to set the period of the Watchdog Timer from 16 ms to 2048 ms.
The available timer periods are shown in the following table and the actual timer periods (at VCC = 5V) are within ±30% of the nominal. The WDT is disabled by Power-on Reset and during Power Down.
It is enabled by setting the WDTEN bit in SFR WCON (address = 96H). The WDT is reset by setting the WDTRST bit in WCON. When the WDT times out without being reset or disabled, an internal RST pulse is generated to reset the CPU before Recover Microcontroller ATMEGA169PV Heximal.
Timer 0 and Timer 1 in the ATMEGA169PV operate the same way as Timer 0 and Timer 1 in the ATMEGA169PV. For further information, see the October 1995 IC Data Book, page 2-45, section titled, “Timer/Counters.”
Timer 2 is a 16 bit Timer/Counter that can operate as either a timer or an event counter.
The type of operation is selected by bit C/T2 in the SFR T2CON (shown in Table 2). Timer 2 has three operating modes: capture, auto-reload (up or down counting), and baud rate generator.
The modes are selected by bits in T2CON, as shown in Table 8. Timer 2 consists of two 8-bit registers, TH2 and TL2.
In the Timer function, the TL2 register is incremented every machine cycle. Since a machine cycle consists of 12 oscillator periods, the count rate is 1/12 of the oscillator frequency before Recover Microcontroller ATMEGA169PV Heximal.
 Break MCU ATMEGA2560PV Code
Break MCU ATMEGA2560PV Code
We can break MCU ATMEGA2560PV code, please view the MCU ATMEGA2560PV features for your reference:
Timer 2 is a 16 bit Timer/Counter that can operate as either a timer or an event counter. The type of operation is selected by bit C/T2 in the SFR T2CON (shown in Table 2). Timer 2 has three operating modes: capture, auto-reload (up or down counting), and baud rate generator.
The modes are selected by bits in T2CON, as shown in Table 8. Timer 2 consists of two 8-bit registers, TH2 and TL2. In the Timer function, the TL2 register is incremented every machine cycle. Since a machine cycle consists of 12 oscillator periods, the count rate is 1/12 of the oscillator frequency if Break MCU ATMEGA2560PV Code.
In the Counter function, the register is incremented in response to a 1-to-0 transition at its corresponding external input pin, T2. In this function, the external input is sampled during S5P2 of every machine cycle. When the samples show a high in one cycle and a low in the next cycle, the count is incremented.
The new count value appears in the register during S3P1 of the cycle following the one in which the transition was detected. Since two machine cycles (24 oscillator periods) are required to recognize a 1-to-0 transition, the maximum count rate is 1/24 of the oscillator frequency after Break MCU ATMEGA2560PV Code.
To ensure that a given level is sampled at least once before it changes, the level should be held for at least one full machine cycle. In the capture mode, two options are selected by bit EXEN2 in T2CON. If EXEN2 = 0, Timer 2 is a 16 bit timer or counter which upon overflow sets bit TF2 in T2CON.
This bit can then be used to generate an interrupt. If EXEN2 = 1, Timer 2 performs the same operation, but a l to-0 transition at external input T2EX also causes the current value in TH2 and TL2 to be captured into RCAP2H and RCAP2L, respectively if break MCU code.
In addition, the transition at T2EX causes bit EXF2 in T2CON to be set. The EXF2 bit, like TF2, can generate an interrupt after Break MCU ATMEGA2560PV Code.
 Reverse Engineering Microcomputer ATMEGA2560L Eeprom
Reverse Engineering Microcomputer ATMEGA2560L Eeprom
We can reverse engineering Microcomputer ATMEGA2560L eeprom, please view the Microcomputer ATMEGA2560L features for your reference:
Timer 2 can be programmed to count up or down when configured in its 16 bit auto-reload mode. This feature is invoked by the DCEN (Down Counter Enable) bit located in the SFR T2MOD.
Upon reset, the DCEN bit is set to 0 so that timer 2 will default to count up. When DCEN is set, Timer 2 can count up or down, depending on the value of the T2EX pin if reverse engineering Microcomputer ATMEGA2560L eeprom.
Figure 2 shows Timer 2 automatically counting up when DCEN = 0. In this mode, two options are selected by bit EXEN2 in T2CON. If EXEN2 = 0, Timer 2 counts up to 0FFFFH and then sets the TF2 bit upon overflow.
The overflow also causes the timer registers to be reloaded with the 16 bit value in RCAP2H and RCAP2L. The values in RCAP2H and RCAP2L are preset by software. If EXEN2 = 1, a 16 bit reload can be triggered either by an overflow or by a 1-to-0 transition at external input T2EX after reverse engineering Microcomputer ATMEGA2560L eeprom.
This transition also sets the EXF2 bit. Both the TF2 and EXF2 bits can generate an interrupt if enabled. Setting the DCEN bit enables Timer 2 to count up or down, as shown in Figure 3. In this mode, the T2EX pin controls the direction of the count. A logic 1 at T2EX makes Timer 2 count up when reverse engineering Microcomputer eeprom.
The timer will overflow at 0FFFFH and set the TF2 bit. This overflow also causes the 16 bit value in RCAP2H and RCAP2L to be reloaded into the timer registers, TH2 and TL2, respectively if reverse engineering Microcomputer ATMEGA2560L eeprom.
A logic 0 at T2EX makes Timer 2 count down. The timer underflows when TH2 and TL2 equal the values stored in RCAP2H and RCAP2L. The underflow sets the TF2 bit and causes 0FFFFH to be reloaded into the timer registers.
The EXF2 bit toggles whenever Timer 2 overflows or underflows and can be used as a 17th bit of resolution. In this operating mode, EXF2 does not flag an interrupt.
 Discover IC Flash
Discover IC Flash
Discover IC Flash content from embedded flash memory of Microcontroller, disable the security fuse bit by crack MCU with focus ion beam technique;
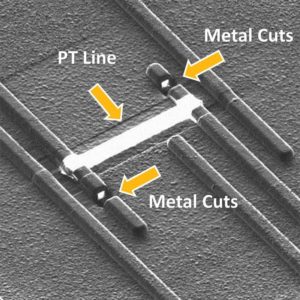
Discover IC Flash content from embedded flash memory of Microcontroller, disable the security fuse bit by crack MCU with focus ion beam technique;
One example of a simple non-invasive chip firmware discovery could be cloning a device based on SRAM FPGA as it is configured at a power-up. The ic attacker could easily connect to the JTAG interface wires used for configuring the chip and, with either an oscilloscope or a logic analyser, grab all the signals. Then he can thoroughly analyse the waveforms and replay the commands in his own design.
He could also slightly change the bitstream to disguise the fact of cloning as usually only half of the FPGA resources are used, leaving a room to fiddle with the configuration without harming device operation. Also the JTAG interface itself gives some freedom in the sequence of the signals being applied so that the waveforms used to configure the pirate copy will look different from the original. In addition, the ic breaker could mix the row addresses during the upload, giving the impression of a completely different design.
 Copy IC Flash
Copy IC Flash
Copy IC Flash program file and eeprom data file from MCU memory, unlock encrypted Microcontroller memory and readout the embedded firmware inside it;
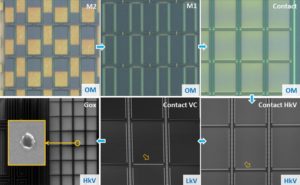
Copy IC Flash program file and eeprom data file from MCU memory, unlock encrypted Microcontroller memory and readout the embedded firmware inside it;
Non-invasive IC Flash copy can be either passive or active. Passive ic attacks, also called side-channel ic decryptions, do not involve any interaction with the attacked device but, usually, observation of its signals and electromagnetic emissions. Examples of such ic breaks are power analysis and timing ic flash copys. Active ic extracts, like brute force and glitch attacks, involve playing with the signals applied to the device including the power supply line.