 Copy IC Flash
Copy IC Flash
Copy IC Flash program file and eeprom data file from MCU memory, unlock encrypted Microcontroller memory and readout the embedded firmware inside it;
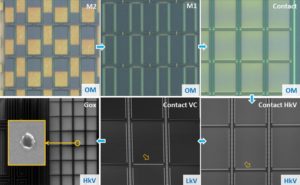
Copy IC Flash program file and eeprom data file from MCU memory, unlock encrypted Microcontroller memory and readout the embedded firmware inside it;
Non-invasive IC Flash copy can be either passive or active. Passive ic attacks, also called side-channel ic decryptions, do not involve any interaction with the attacked device but, usually, observation of its signals and electromagnetic emissions. Examples of such ic breaks are power analysis and timing ic flash copys. Active ic extracts, like brute force and glitch attacks, involve playing with the signals applied to the device including the power supply line.