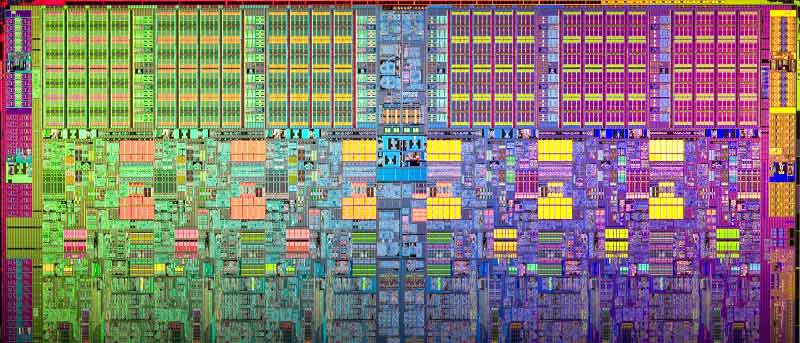
Recover IC Program
Recover IC Program
Recover IC Program from secured MCU flash memory, the fuse bit of microcontroller will be cut by focus ion beam which one of the most commonly method for MCU crack and then copy code to new microprocesor;
Non-invasive ic attacks can be either passive or active. Passive ic cracks, also called side-channel IC code decoding, do not involve any interaction with the ic recover program device but, usually, observation of its signals and electromagnetic emissions. Examples of such mcu breaking are power analysis and timing attacks. Active ic cracks, like brute force and glitch attacks, involve playing with the signals applied to the device including the power supply line.
One example of a simple non-invasive recover ic program could be cloning a device based on SRAM FPGA as it is configured at a power-up. The ic program recover could easily connect to the JTAG interface wires used for configuring the chip and, with either an oscilloscope or a logic analyser, grab all the signals.
Then he can thoroughly analyse the waveforms and replay the commands in his own design. He could also slightly change the bitstream to disguise the fact of cloning as usually only half of the FPGA resources are used, leaving a room to fiddle with the configuration without harming device operation.
Also the JTAG interface itself gives some freedom in the sequence of the signals being applied so that the waveforms used to configure the pirate copy will look different from the original. In addition, the ic program recover could mix the row addresses during the upload, giving the impression of a completely different design.
 Decrypt IC Program
Decrypt IC Program
Decrypt IC Program from locked microcontroller’s flash and eeprom memory, and then copy firmware out from MCU by programmer, rewrite the heximal to new MCU for cloning;

A non-invasive ic crack does not require any initial preparations of the device under test. The ic attacker can either tap the wires to the device, or plug it into a test circuit for the analysis. Once found, these mcu cracks could be easily scaled and their reproduction does not involve very much cost.
In addition, no tamper evidence is left after they are applied. Therefore they are considered to be the most serious threat to the hardware security of any device. At the same time it usually takes a lot of time and effort to find an ic program decryption on any particular device.
This often involves reverse engineering the device in the sense of either disassembling its software or understanding its hardware layout.
 Recover Microprocessor ATmega2561V Code
Recover Microprocessor ATmega2561V Code
Recover Microprocessor ATmega2561V Code is a process to extract program and data from MCU ATmega2561V memory after crack microcontroller tamper resistance system;

Port E is an 8-bit bi-directional I/O port with internal pull-up resistors (selected for each bit). The Port E output buffers have symmetrical drive characteristics with both high sink and source capability.
As inputs, Port E pins that are externally pulled low will source current if the pull-up resistors are activated when recover microprocessor code.
The Port E pins are tri-stated when a reset condition becomes active, even if the clock is not running. Port F serves as analog inputs to the A/D Converter. Port F also serves as an 8-bit bi-directional I/O port, if the A/D Converter is not used if attack microprocessor pic16c63a hex.
Port pins can provide internal pull-up resistors (selected for each bit). The Port F output buffers have symmetrical drive characteristics with both high sink and source capability. As inputs, Port F pins that are externally pulled low will source current if the pull-up resistors are activated.
The Port F pins are tri-stated when a reset condition becomes active, even if the clock is not running. If the JTAG interface is enabled, the pull-up resistors on pins PF7(TDI), PF5(TMS), and PF4(TCK) will be activated even if a reset occurs.
Port F also serves the functions of the JTAG interface. Port G is a 6-bit I/O port with internal pull-up resistors (selected for each bit). The Port G output buffers have symmetrical drive characteristics with both high sink and source capability when attack chip atmega8a binary.
As inputs, Port G pins that are externally pulled low will source current if the pull-up resistors are activated. The Port G pins are tri-stated when a reset condition becomes active, even if the clock is not running.
Port G also serves the functions of various special features of the ATmega2561 as listed on page 102.
Port H is a 8-bit bi-directional I/O port with internal pull-up resistors (selected for each bit). The Port H output buffers have symmetrical drive characteristics with both high sink and source capability. As inputs, Port H pins that are externally pulled low will source current if the pull-up resistors are activated. The Port H pins are tri-stated when a reset condition becomes active, even if the clock is not running before RECOVER MCU.
Port J is a 8-bit bi-directional I/O port with internal pull-up resistors (selected for each bit). The Port J output buffers have symmetrical drive characteristics with both high sink and source capability. As inputs, Port J pins that are externally pulled low will source current if the pull-up resistors are activated after recover microprocessor code.
The Port J pins are tri-stated when a reset condition becomes active, even if the clock is not running.
 Break Microcontroller ATtiny48 Flash
Break Microcontroller ATtiny48 Flash
Break Microcontroller ATtiny48 Flash memory and readout code from MCU, the file format of firmware will be binary or heximal;
Port K serves as analog inputs to the A/D Converter.
Port K is a 8-bit bi-directional I/O port with internal pull-up resistors (selected for each bit). The Port K output buffers have symmetrical drive characteristics with both high sink and source capability. As inputs, Port K pins that are externally pulled low will source current if the pull-up resistors are activated. The Port K pins are tri-stated when a reset condition becomes active, even if the clock is not running.
Port L is a 8-bit bi-directional I/O port with internal pull-up resistors (selected for each bit). The Port L output buffers have symmetrical drive characteristics with both high sink and source capability.
As inputs, Port L pins that are externally pulled low will source current if the pull-up resistors are activated. The Port L pins are tri-stated when a reset condition becomes active, even if the clock is not running.
Reset input. A low level on this pin for longer than the minimum pulse length will generate a reset, even if the clock is not running. The minimum pulse length is given in Table 23 on page 58. Shorter pulses are not guaranteed to generate a reset when break Microcontroller pic18f8722 flash.
Input to the inverting Oscillator amplifier and input to the internal clock operating circuit. Output from the inverting Oscillator amplifier. AVCC is the supply voltage pin for Port F and the A/D Converter if break Microcontroller flash.
It should be externally connected to VCC, even if the ADC is not used. If the ADC is used, it should be connected to VCC through a low-pass filter.
This is the analog reference pin for the A/D Converter. This documentation contains simple code examples that briefly show how to use various parts of the device. Be aware that not all C compiler vendors include bit definitions in the header files and interrupt handling in C is compiler dependent.
Please confirm with the C compiler documentation for more details. These code examples assume that the part specific header file is included before compilation. For I/O registers located in extended I/O map, “IN”, “OUT”, “SBIS”, “SBIC”, “CBI”, and “SBI” instructions must be replaced with instructions that allow access to extended I/O. Typically “LDS” and “STS” combined with “SBRS”, “SBRC”, “SBR”, and “CBR”.
 Break IC Program
Break IC Program
Break IC secured memory and extract program from MCU flash memory and eeprom memory, unlock microcontroller needs to figure out its internal scheme in order to locate the security fuse bit;
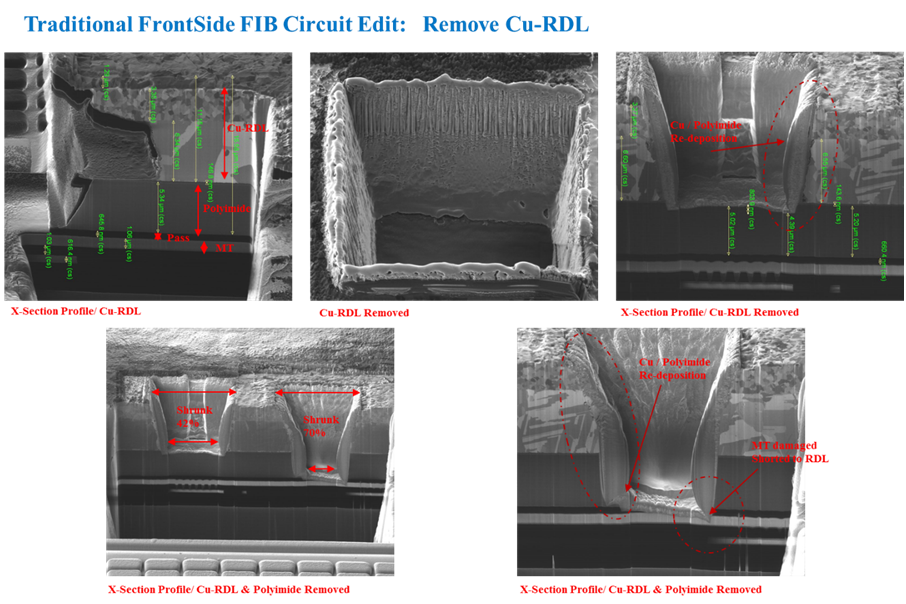
Fault injection IC program breaks done in a semi-invasive manner which can be used to modify the contents of SRAM and change the state of any individual transistor inside the chip. That gives almost unlimited capabilities to the ic breaker in getting control over the chip operation and abusing the protection mechanism.
Compared to non-invasive ic attacks, semi-invasive ic cracks are harder to implement as they require decapsulation of the chip. However, very much less expensive equipment is needed than for invasive mcu cracks. These ic program breaks can be performed in a reasonably short period of time. Also they are scalable to a certain extent, and the skills and knowledge required to perform them can be easily and quickly acquired. Some of these ic attacks, such as an exhaustive search for a security fuse, can be automated. If compared to invasive mcu cracks, the semi-invasive kind do not normally require precise positioning for success because they are normally applied to a whole transistor or even a group of transistors rather than to a single wire inside the chip.
 IC Program Crack
IC Program Crack
Semi-invasive IC program crack are not entirely new. UV light has been used to disable security fuses in EPROM and OTP microcontrollers for many years.
Modern microcontrollers are less susceptible to this MCU cracking as they were designed to withstand it. More information on the evolution of defences against UV breaking in microcontrollers later. Advanced imaging techniques can be considered as semi-invasive as well.
This includes various kinds of microscopy such as infrared, laser scanning and thermoimaging. Some of them can be applied from the rear side of the chip which is very useful for modern chips with multiple metal layer design. Some of these techniques allow observation of the state of each individual transistor inside the chip.
 IC Program Attack
IC Program Attack
There is a large gap between previously discussed non-invasive ic program attack and invasive microcontroller unlocking, many mcu crackers fall into this gap, being not so expensive as classical penetrative invasive ic attacks but as easily repeatable as non-invasive program attacks.
Therefore we decided to define and introduce a new class of program attack called semi-invasive. Like invasive chip program attacks, they require depackaging the chip in order to get access to its surface. However, the passivation layer of the chip remains intact, as semi-invasive methods do not require depassivation or creating contacts to the internal lines. This is because microprobing is not used for this mcu program attack technology and thus such expensive tools as laser cutters and FIBs are not required.
 Extract IC Program
Extract IC Program
Extract IC program execution has greater complexity, some of them can be done without expensive laboratory equipment.
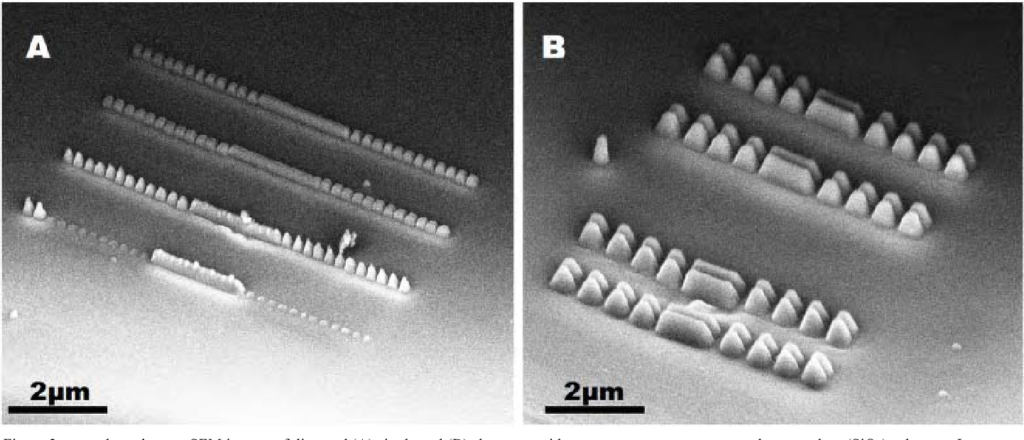
Low-budget MCU breakers are likely to get a cheap solution on the second-hand market for semiconductor test equipment. With patience and skill, it should not be too difficult to assemble all the required tools for under ten thousand pounds by buying a second-hand microscope and using self-designed micropositioners.
Invasive IC crackers start with the removal of the chip package. Once the chip is opened it is possible to perform probing or modifying microcontroller. The most important tool for invasive IC code extraction is a microprobing workstation. Its major component is a special optical microscope with a long working distance objective lens.
Micropositioners are installed on a stable platform around the chip test socket and allow the movement of probe arms, with submicron precision, over a chip surface. A probing needle with an elastic hair at the end is installed on each arm and allows electrical contact to on-chip bus lines without damaging them.
 Reverse Engineering MCU ATtiny48V Eeprom
Reverse Engineering MCU ATtiny48V Eeprom
Reverse Engineering MCU ATtiny48V Eeprom physical structure in the reverse order of microcontroller ATtiny48v manufacturing, security fuse bit can be located and crack microcontroller‘s bit, so the firmware can be readout from MCU memory;

This section discusses the AVR core architecture in general. The main function of the CPU core is to ensure correct program execution. The CPU must therefore be able to access memories, perform calculations, control peripherals, and handle interrupts. In order to maximize performance and parallelism, the AVR uses a Harvard architecture – with separate memories and buses for program and data. Instructions in the program memory are executed with a single level pipelining.
While one instruction is being executed, the next instruction is pre-fetched from the program memory. This concept enables instructions to be executed in every clock cycle. The program memory is In System Reprogrammable eeprom memory. The fast-access Register File contains 32 x 8-bit general purpose working registers with a single clock cycle access time.
This allows single-cycle Arithmetic Logic Unit (ALU) operation.
In a typMCUal ALU operation, two operands are output from the Register File, the operation is executed, and the result is stored back in the Register File – in one clock cycle. Six of the 32 registers can be used as three 16-bit indirect address register pointers for Data Space addressing – enabling effMCUient address calculations.
One of the these address pointers can also be used as an address pointer for look up tables in eeprom program memory. These added function registers are the 16-bit X-, Y-, and Z-register, described later in this section.
The ALU supports arithmet and logic operations between registers or between a constant and a register. Single register operations can also be executed in the ALU. After an arithmetic operation, the Status Register is updated to reflect information about the result of the operation.
Program flow is provided by conditional and unconditional jump and call instructions, able to directly address the whole address space. Most AVR instructions have a single 16-bit word format. Every program memory address contains a 16- or 32-bit instruction after REVERSE ENGINEERING MICROCONTROLLER.
 Reverse Engineering IC Firmware
Reverse Engineering IC Firmware
The next possible way of reverse engineering IC firmware from a device is playing around with its interface signals and access protocols. Also, if a security protocol is wrongly implemented, that leaves a hole for the ic reverse engineering firmware people to exploit.
Some microcontrollers and smartcards have a factory-test interface that provides access to on-chip memory and allows the manufacturer to test the device. If IC code extraction process can find a way of exploiting this interface, he can easily extract the information stored inside the chip.
Normally information on test circuits is kept secret by the manufacturer, but an MCU cracker can try applying different voltages and logic levels to the pins in the hope that it will put it into test mode. This sometimes works for microcontrollers but in smartcards such test circuitry is usually destroyed after use.
Also, embedded software developers sometimes implement functions that allow downloading from internal memory for test and update purposes. That must be done in a way that prevents any access to the code without proper authentication, or so that the code can be sent out in encrypted form only.