Archive for May, 2013
 Read CPLD Chip Microcontroller IC JED
Read CPLD Chip Microcontroller IC JED
Read CPLD Chip Microcontroller IC JED File out from CPLD chip memory, copy JED file to new CPLD chip which can provide the same functions as original one after reset the status of CPLD by Microcontroller unlock skill;
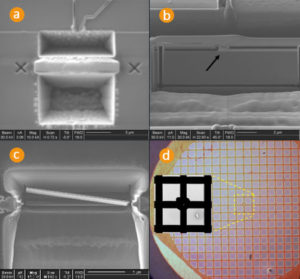
Read CPLD Chip Microcontroller IC JED File out from CPLD chip memory, copy JED file to new CPLD chip which can provide the same functions as original one after reset the status of CPLD by Microcontroller unlock skill
Our next experiment was done to the PIC16F84A microcontroller which has Flash program memory and EEPROM data memory. A similar test sequence was applied with the only difference that electrical erasing was used. A huge difference in the memory behaviour can be observed. The memory erase starts 65 µs after the ‘chip erase’ command was received and by 75 µs the memory is erased.
However, this time changes if the temperature or the supply voltage is changed. For example, if the chip is heated to 35°C the memory erase starts at 60 µs and is finished by 70 µs. The security fuse requires at least 125 µs to be erased giving at least five times excess for reliable memory erase. Reducing the power supply voltage increases the erase time for both the memory and the fuse erase, so that the ratio remains practically the same.
It should be mentioned that unless terminated by the hardware reset, the chip erase operation lasts for at least 1 ms. Both this fact and the fast erase time give an impression that EEPROM and Flash memories have fewer problems with data remanence and therefore should offer better security protection. We decided to investigate whether this is true or not.
 Copy CPLD IC Code
Copy CPLD IC Code
Copy CPLD IC Code from CPLD chip memory is a reverse CPLD manufacturing process, original master CPLD will be cracked and firmware inside memory of CPLD can be readout directly;
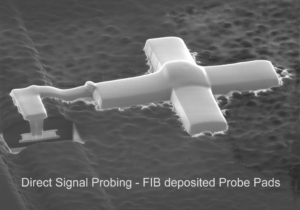
Copy CPLD IC Code from CPLD chip memory is a reverse CPLD manufacturing process, original master CPLD will be cracked and firmware inside memory of CPLD can be readout directly
Normally, the programming of an EPROM memory is controlled by external signals and all the timings should be supplied by a programmer unit. This gives an opportunity for the attacker to inject charge into the floating gate thus shifting the threshold level enough to read the memory contents when the security fuse is inactive.
Such a trick is virtually impossible to apply to modern EEPROM and Flash memory devices for several reasons. First, the programming is fully controlled by the on-chip hardware circuit. Second, the programming of EEPROM and Flash cells is normally performed by using much faster Fowler-Nordheim tunnelling rather than CHE injection. As a result it is very hard to control the exact amount of charge being placed into the cell. Also, the temperature and the supply voltage affect this process making it even harder to control.
 Copy CPLD MCU Software Data
Copy CPLD MCU Software Data
Copy CPLD MCU Software Data from flash memory and rewrite the program to new CPLD chip which can provide the same functions as original CPLD chip after MCU Cracking;
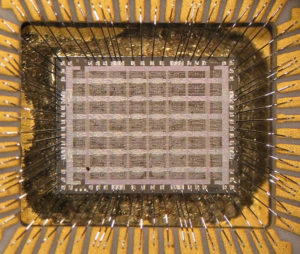
Copy CPLD MCU Software Data from flash memory and rewrite the program to new CPLD chip which can provide the same functions as original CPLD chip after MCU Cracking
There is another trick that makes recovery of memory contents possible, even when there is no overlap between the erased security fuse and non-corrupted memory content at the time of erasure. For example, we found that newer samples of the same chip will start to corrupt the memory before the security fuse is erased. In this case a power glitch cannot be used to recover information from the memory. What can be done instead is a careful adjustment of the threshold voltage in the cell’s transistor. It is possible to inject a certain portion of charge into the floating gate by carefully controlling the memory programming time.
 Extract AVR Chip Software & Data
Extract AVR Chip Software & Data
Extract AVR Chip Software Data, the program from flash memory and data from eeprom can be readout from AVR MCU after unlock AVR microcontroller protective fuse bit;
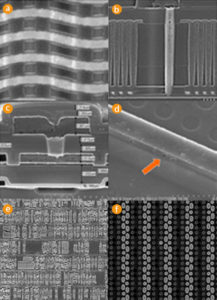
Extract AVR Chip Software & Data, the program from flash memory and data from eeprom can be readout from AVR MCU after unlock AVR microcontroller protective fuse bit
There is another trick that makes recovery of memory contents possible, even when there is no overlap between the erased security fuse and non-corrupted memory content at the time of erasure. For example, we found that newer samples of the same chip will start to corrupt the memory before the security fuse is erased. In this case a power glitch cannot be used to recover information from the memory.
What can be done instead is a careful adjustment of the threshold voltage in the cell’s transistor. It is possible to inject a certain portion of charge into the floating gate by carefully controlling the memory programming time. Normally, the programming of an EPROM memory is controlled by external signals and all the timings should be supplied by a programmer unit.
This gives an opportunity for the attacker to inject charge into the floating gate thus shifting the threshold level enough to read the memory contents when the security fuse is inactive. Such a trick is virtually impossible to apply to modern EEPROM and Flash memory devices for several reasons. First, the programming is fully controlled by the on-chip hardware circuit.
Second, the programming of EEPROM and Flash cells is normally performed by using much faster Fowler-Nordheim tunnelling rather than CHE injection. As a result it is very hard to control the exact amount of charge being placed into the cell. Also, the temperature and the supply voltage affect this process making it even harder to control.