Posts Tagged ‘extract fpga ic heximal data’
 Reverse LATTICE CPLD Source code
Reverse LATTICE CPLD Source code
Reverse LATTICE CPLD source code is a process to extract jed file from encrypted Lattice CPLD, using physical MCU invasive cracking method include decapsulation and focus ion beam can help to fulfill the task;
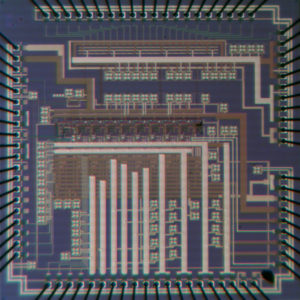
Reverse LATTICE CPLD source code is a process to extract jed file from encrypted Lattice CPLD, using physical MCU invasive cracking method include decapsulation and focus ion beam can help to fulfill the task
The same memory type but built with newer technologies such as 0.9 µm in the Microchip PIC16CR57 microcontroller [124] and 1.0 µm in the Motorola MC68HC705C9A microcontroller [23] requires deprocessing because the top bit-line metal wires obstruct observation of the transistors.
NAND Mask ROM memory type with metal layer programming was used in the NEC µPD78F9116 microcontroller [125] fabricated with 0.35 µm technology. As all the internal layers were planarised, deeper layers cannot be observed unless the top metal layer is removed.
This was accomplished by using Nitrox etching for the passivation layer followed by treatment in a 33% water solution of KOH to etch the top aluminium metal layer but preserving the interconnection layer which is probably made out of tungsten (because when the HCl solution was used to etch the top metal layer, the interconnection layer was etched away as well).