 Extract MCU Firmware
Extract MCU Firmware
Extract MCU Firmware from program memory and data memory after remove the tamper resistance system of microcontroller and replicate the code to new MCU;
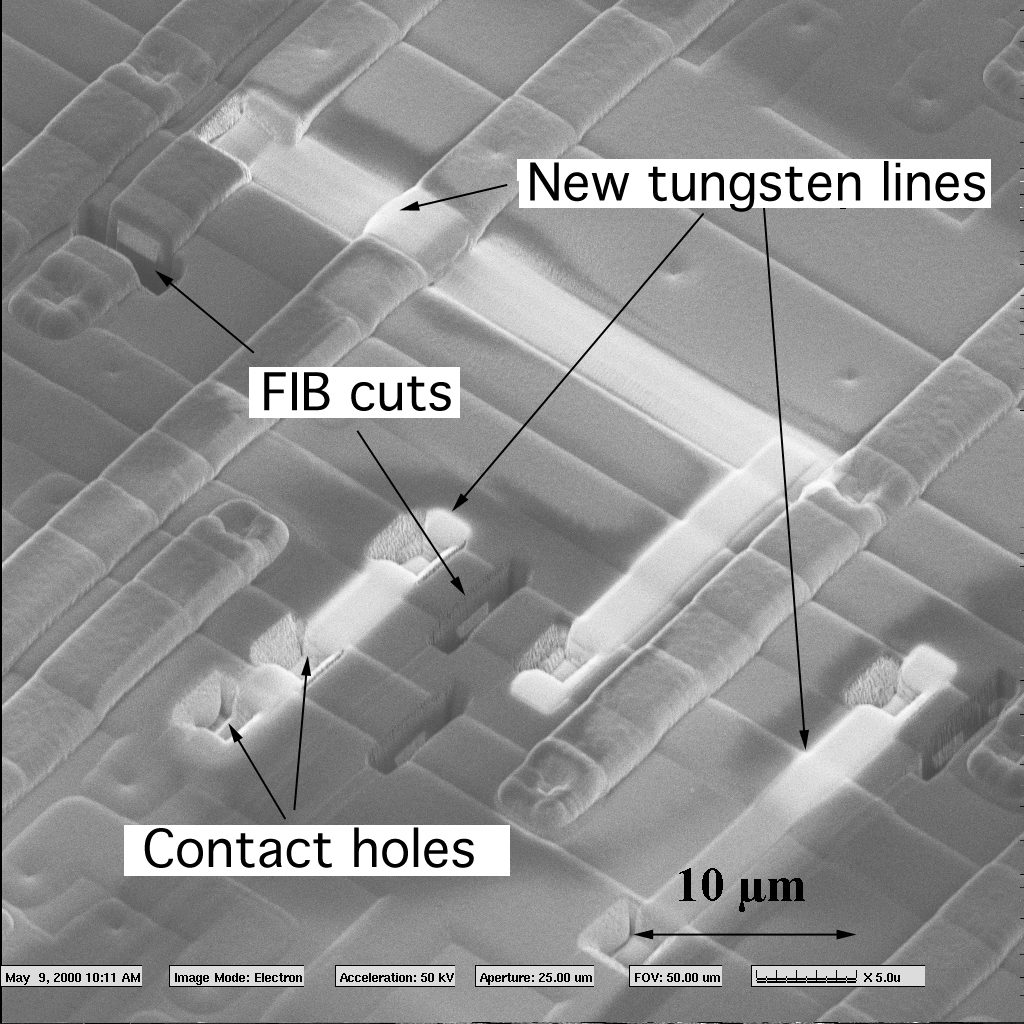
Some manufacturers intentionally do not provide any programming specifications for their MCU microcontrollers. That does not give very good protection on its own, and only slightly increases the cost of microcontroller reverse engineering, because this MCU firmware can be extracted by observing the signals applied to the IC chip during programming in a development kit or in a universal programmer.
Obviously, for the highest security, the system would not have any programming interface at all, and would not provide any access to stored data. This is normally the case for Mask ROM microcontrollers and smartcards. The only practical ways of attack chip flash in this case would be either to microprobe the data bus to recover the information or use power analysis and glitch attacks to exploit any vulnerability in software.
Relatively high security can be obtained when a microcontroller is user programmable but does not provide any read-back facility – only verify and write check, for example in the NEC 78K0S family Flash microcontrollers.
Of course this should be implemented properly to avoid the situation where the microprocessor decryption can force the system to verify one byte at a time. In this case he would need on average 128 attempts per byte (28 × 0.5) and assuming the byte access cycle is 5 ms it will take him less than a day to extract the contents of the memory, which is usually between 4 Kb and 64 Kb. Even if the verify operation is applied to large blocks of data, the mcu firmware extraction could try glitch attacks to reduce the cycle to a single byte.
 Read MCU Code
Read MCU Code
Read MCU Code out from embedded and secured flash memory and eeprom memory can help to recover the content from master microcontroller;
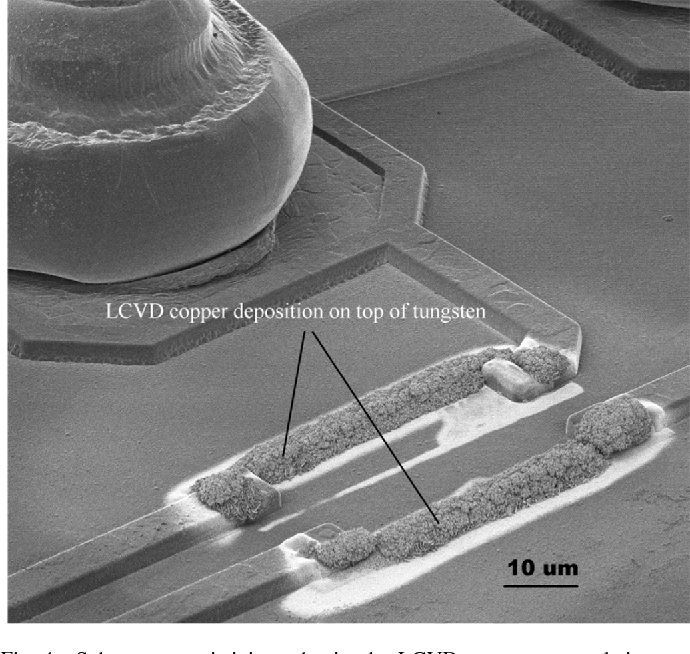
Another memory type used in all Microcontroller MCUs (mainly as a register file memory and operational memory) is SRAM. It is also used in secure microcontroller MCUs such as the Dallas DS5002FP and JAVA iButtons where the information should disappear quickly if atampering attempt is sensed. An SRAM memory cell consists of six transistors, four of which create a flip-flop while the other two are used for accessing the cell inside the array.
SRAM memory offers very good security protection, as the information from it can be easily erased by disconnecting the power supply if the alarm is triggered. Performing invasive or semi-invasive MCU Crack is very problematic because any attempt to extract microcontroller code surface would very likely destroy the data. For example, decapsulation requires very strong acids to be used which a
re conductive and cannot be used on a powered up chip. Even if chip atmega2561v attacker manages to access the die, the state of its transistors cannot be observed optically. Microprobing is difficult because the internal wires are buried under top metal bit-lines, ground and power supply wires. The only practical way to access the memory is from the rear side of the chip die, but this requires more expensive equipment and a highly skilled IC Attacker.
Meantime, there are some semi-invasive techniques that allow observation of the memory state, but require special laser scanning microscopes. At the same time non-invasive mcu attacks can be used to exploit any problems that might exist in the memory interface, as happened with the Dallas Semiconductor secure microcontrolle.
Data remanence could cause some problems to SRAM security as well. At temperatures below 0˚C some samples of the SRAM chips retain information for hours. But, in general, SRAM memory offers a very good level of protection and low-temperature attacks can be avoided by placing temperature sensors into the secure module enclosure as in the IBM 4758 cryptoprocessor.
 Break Secured IC PIC16F716 Firmware
Break Secured IC PIC16F716 Firmware
Break Secured IC PIC16F716 flash memory, cut off microcontroller PIC16F716 security fuse bit and extract firmware from MCU.
The PIC16F7X devices have a 13-bit program counter capable of addressing an 8K word x 14-bit program memory space. The PIC16F77/76 devices have 8K words of FLASH program memory and the PIC16F73/74 devices have 4K words when copy ic atmega8l heximal.
The program memory maps for PIC16F7X devices are shown in Figure 2-1. Accessing a location above the physically implemented address will cause a wrap around Firmware.
The RESET Vector is at 0000h and the Interrupt Vector is at 0004h. The Data Memory is partitioned into multiple banks, which contain the General Purpose Registers and the Special Function Registers.
Bits RP1 (STATUS<6>) and RP0 (STATUS<5>) are the bank select bits: Each bank extends up to 7Fh (128 bytes). The lower locations of each bank are reserved for the Special Function Registers after copy mcu pic32mx440f512 bin.
Above the Special Function Registers are General Purpose Registers, implemented as static RAM. All implemented banks contain Special Function Registers.
Some frequently used Special Function Registers from one bank may be mirrored in another bank for firmware reduction and quicker access. The register file (shown in Figure 2-2 and Figure 2-3) can be accessed either directly, or indirectly, through the File Select Register FSR Firmware.
The Special Function Registers are registers used by the CPU and peripheral modules for controlling the desired operation of the device. These registers are implemented as static RAM after IC breaking.
The Special Function Registers can be classified into two sets: core (CPU) and peripheral. Those registers associated with the core functions are described in detail in this section. Those related to the operation of the peripheral features are described in detail in the peripheral feature section.
 Reverse Microchip MCU PIC16LF77 Flash
Reverse Microchip MCU PIC16LF77 Flash
Reverse Microchip MCU PIC16LF77 Flash memory and readout hex of microcontroller PIC16LF77, status of processor PIC16LF77 can be opened and unlocking MCU’s tamper resistance system;
Low power, high speed CMOS FLASH technology
Fully static design
Wide operating voltage range: 2.0V to 5.5V
High Sink/Source Current: 25 mA
Industrial temperature range
Low power consumption:
– < 2 mA typical @ 5V, 4 MHz
– 20 µA typical @ 3V, 32 kHz
– < 1 µA typical standby current
PIC16F73/76 devices are available only in 28-pin packages, while PIC16F77 devices are available in 40-pin and 44-pin packages.
All devices in the PIC16F7X family share common architecture, with the following differences:
The PIC16F73 and PIC16F76 have one-half of the total on-chip memory of the PIC16LF77
The 28-pin devices have 3 I/O ports, while the 40/44-pin devices have 5
The 28-pin devices have 11 interrupts, while the 40/44-pin devices have 12
The 28-pin devices have 5 A/D input channels, while the 40/44-pin devices have 8
The Parallel Slave Port is implemented only on the 40/44-pin devices before Microchip mcu chip recovering
Additional information may be found in the PICmicro™ Mid-Range Reference Manual (DS33023), which may be obtained from your local Microchip Sales Representative or downloaded from the Microchip website.
The Reference Manual should be considered a complementary document to this data sheet, and is highly recommended reading for a better understanding of the device architecture and operation of the peripheral modules of Microchip mcu ST62T15C6 firmware attacking.
 MCU Code Restoration
MCU Code Restoration
MCU Code Restoration can help engineer to recover mcu heximal from secured memory include flash and eeprom one after crack microcontroller;
Another big problem for EPROM, EEPROM and Flash memories that affects the hardware security of the MCU devices is data remanence. Many MCUs with these types of memory have a security fuse which, once activated, cannot be reset until the whole memory content is first erased. Manufacturers put a lot of effort into hardware design to ensure that the security fuse will not be deactivated by manipulation of external signals such as power glitches. They made very good progress, and very few of the modern MCUs can be broken using tricks such as applying power glitches during the chip erase operation to terminate the memory erase without affecting the erase of the security fuse, or exposing the chip to UV light for long enough to erase the security fuse but not long enough to destroy the memory source code contents.
But recent revisions of MCUs are not sensitive to such IC code extraction. In modern chips, an additional voltage monitoring circuit is usually implemented, causing a reset of the hardware programming interface or preventing any write/erase operations below or above certain voltages. What was wrongly assumed is that information must disappear from the memory after it was erased. In fact some traces of the data are still left after the erase operation, and to get the information back we just have to find the right method to measure the residual charge on a floating gate, or a threshold of a memory transistor.
This is not an easy task, but if the security fuse was deactivated during the chip erase operation, the memory can be accessed normally. That allows engineer to recover ic eeprom program and measure the response from each transistor inside the array by sequential reading of each memory location and microprobing the internal memory bus.
Of course it is not a trivial task, but a determined and experienced mcu program breaker can do this. In some MCUs the threshold level of each transistor can be measured in fully non-invasive mcu code restoration way by playing with the interface and power supply voltages. This is possible because very often the memory sense circuit uses the power supply voltage as a reference.
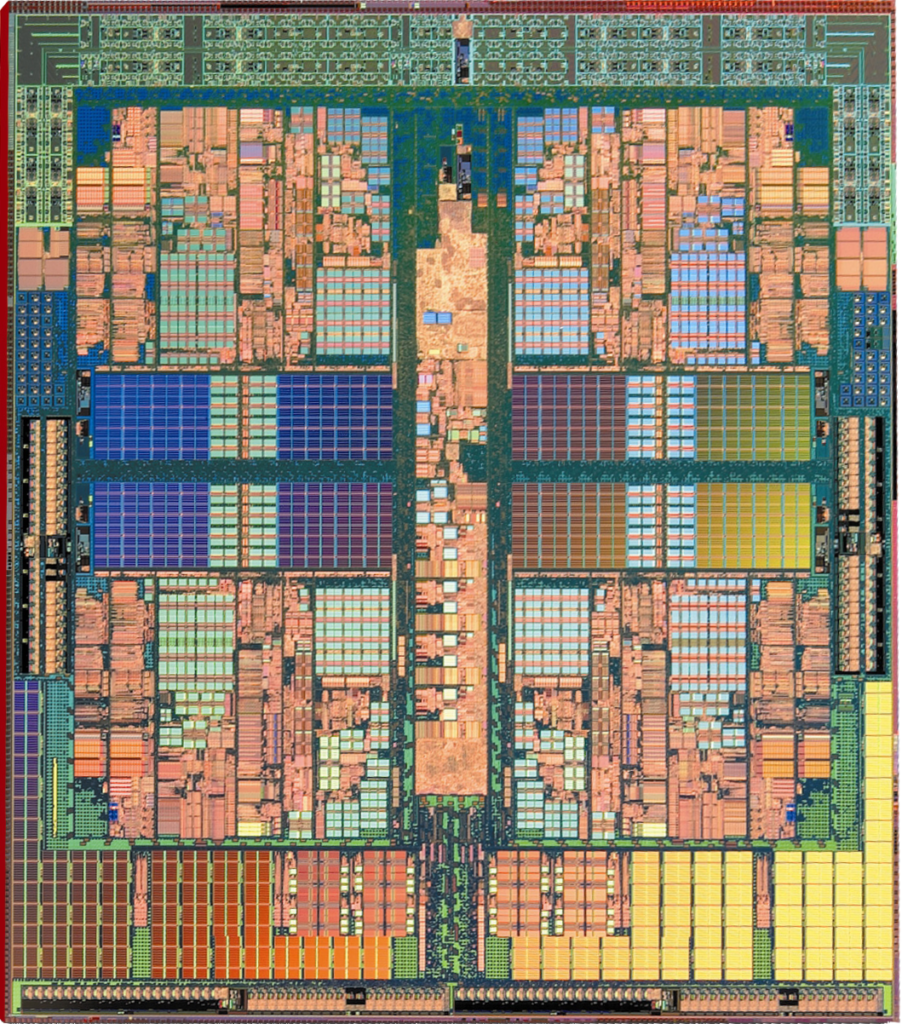
 EPROM advantage when MCU Code Decryption
EPROM advantage when MCU Code Decryption
MCU Code Decryption happens after extract microcontroller heximal file out from its embedded program and data memory through unlock MCU method;
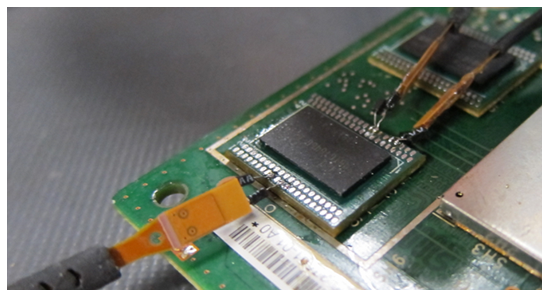
In terms of non-invasive MCU Code Decryption, EPROM memory has some advantages over EEPROM and Flash memories as it is more robust against power glitch decryptions. This happens because it has a simpler structure, larger cell size, thicker gate oxide and no on-chip high-voltage charge pumps.
The sense amplifiers used to distinguish between ‘0’ and ‘1’ logic states are much simpler in EPROM and less sensitive to the power supply voltage. Against semi-invasive mcu source code decryption, EPROM memory is also better than EEPROM and Flash. For example, the fault injection decryption that will be discussed later can be used to modify the contents of the cell but for EPROM much higher power is required.
That makes OTP microcontrollers more attractive in the applications where high security is required. Unfortunately modern microcontrollers do not use this type of memory any more as it cannot be reprogrammed, has lower density than the Flash memory and is thus more expensive. That forces semiconductor manufacturers to introduce additional protection against unauthorised access to the memory contents.
For example, modern smartcards do not have hardware control for access to the on-chip Flash and EERPOM memories, but only a bootstrap loader located in the Flash memory that overwrites itself during first initialisation, eliminating any possible access to the information (unless implemented by the customer). Hardware access to the memory has multi-level security protection ensuring that access will not be granted unless all the requirements are met. In some microcontrollers, very sophisticated access password protection is implemented.
 Recovery Microcontroller PIC16LF76 Firmware
Recovery Microcontroller PIC16LF76 Firmware
Recovery Microcontroller PIC16LF76 Firmware from flash memory and eeprom memory, crack MCU PIC16LF76 protective system and extract firmware from PIC16LF76 processor;
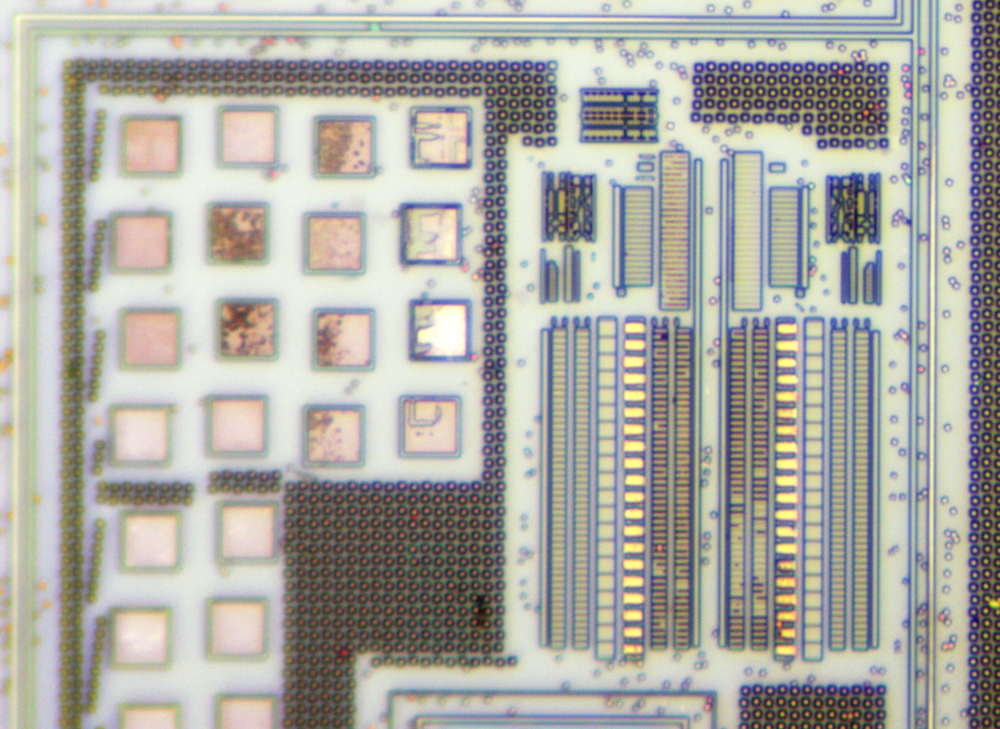
PIC16LF76 devices are available only in 28-pin packages, while PIC16LF76 devices are available in 40-pin and 44-pin packages. All devices in the PIC16F7X family share common architecture, with the following differences:
The PIC16LF76 have one-half of the total on-chip memory of the PIC16LF76
The 28-pin devices have 3 I/O ports, while the 40/44-pin devices have 5 if microcontroller samsung s3f9454 software breaking.
The 28-pin devices have 11 interrupts, while the 40/44-pin devices have 12
The 28-pin devices have 5 A/D input channels, while the 40/44-pin devices have 8.
The Parallel Slave Port is implemented only on the 40/44-pin devices
The available features are summarized in Table 1-1.
Block diagrams of the PIC16LF76 after Recovery.
Additional information may be found in the PICmicro™
Mid-Range Reference Manual (DS33023), which may be obtained from your local Microchip Sales Representative or downloaded from the Microchip website.
The Reference Manual should be considered a complementary document to this data sheet, and is highly recommended recoverying for a better understanding of the device architecture and operation of the peripheral modules Mcu pic16f688 software reading.
There are two memory blocks in each of these PICmicro® MICROCONTROLLERs. The Program Memory and Data Memory have separate buses so that concurrent access can occur and is detailed in this section.
The Program Memory can be recovery internally by user code (see Section 3.0). Additional information on device memory may be found in the PICmicro Mid-Range Reference Manual (DS33023).
 MCU Code Reverse Engineering Roadmap
MCU Code Reverse Engineering Roadmap
MCU Code Reverse Engineering is actually a process of reprogramming microcontroller in the reverse order, microcontroller will be reset by unlocking technique to ensure the heximal reading from flash memory;

Technological progress on its own is increasing the costs to MCU reverse engineering. Ten years ago it was possible to use a laser cutter and a simple probing station to get access to any point on the chip surface, but for modern deep submicron semiconductor chips very sophisticated and expensive technologies must be used.
That excludes most potential MCU code extraction. For example, the structure of the Microchip PIC16F877 microcontroller can be easily observed and reverse engineered under a microscope.
The second metal layer and polysilicon layer can still be seen even if buried under the top metal layer. This is possible because each subsequent layer in the fabrication process follows the shape of the previous layer. Under a microscope the observer sees not only the highest layer but also edges that reveal the structure of the deeper layers.
In 0.5 µm and smaller technologies, for example in the Microchip PIC16F877A microcontroller, each predecessor layer is planarised using chemical-mechanical planarisation (CMP) process before applying the next layer. As a result the top metal layer does not show the impact of the deeper layers. The only way to reveal the structure of the deeper layers is by removing the top metal layers either mechanically or chemically.
As can be seen from all the shown examples, hardware security in microcontrollers and smartcards is being constantly improved. Because the tools for mcu code reverse engineering are becoming more sophisticated, better and better security protection is required. Rapid co-evolution is driven by this continuous battle between mcu manufacturers and mcu code reverse engineer.
Another threat that must be considered is that a great deal of second-hand semiconductor manufacturing and testing equipment appears on the market. It cannot be used to reverse engineering high-end products, but should be enough to reverse engineering MCUs manufactured with older technology. For example, while 90 nm manufacturing technology is currently leading-edge, most microcontrollers are produced with 0.35 µm technology and smartcards with 0.25 µm technology.
 Break IC PIC16LF74 Memory
Break IC PIC16LF74 Memory
Break IC PIC16LF74 Memory needs to cut off security fuse bit by focus ion beam and readout microcontroller PIC16LF74 progrm;
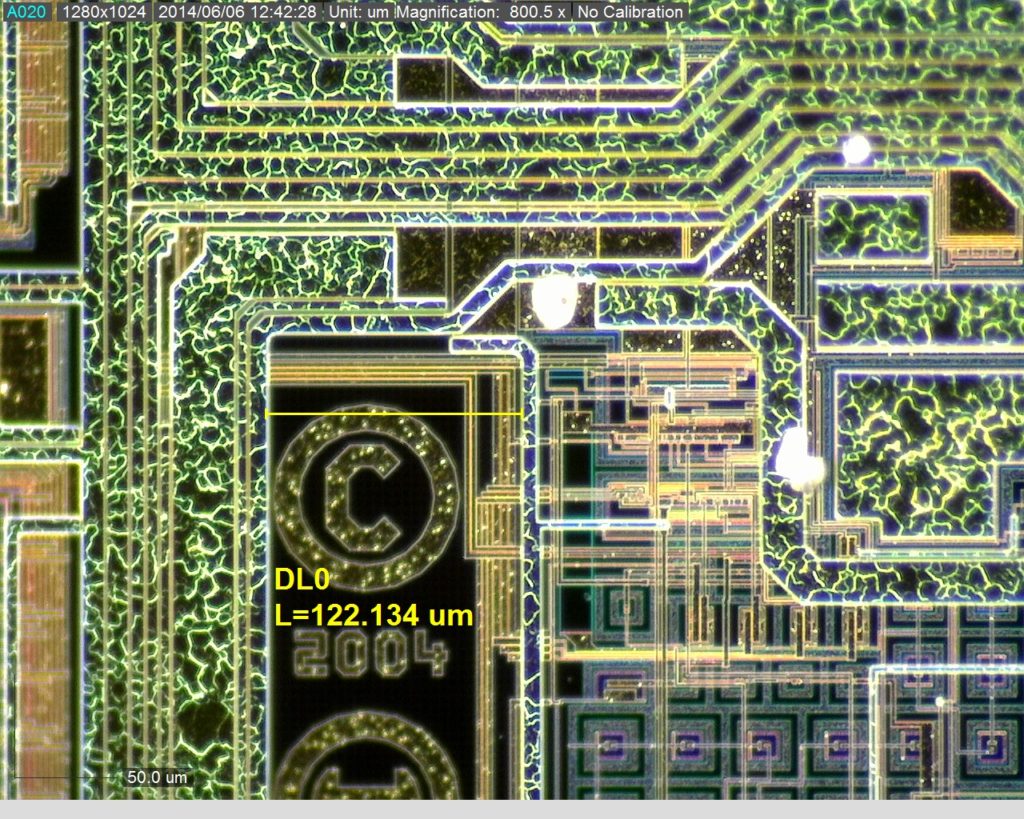
High performance RISC CPU
Only 35 single word instructions to learn
All single cycle instructions except for program branches which are two-cycle
Operating speed: DC – 20 MHz clock input DC – 200 ns instruction cycle when Break IC
Up to 8K x 14 words of FLASH Program Memory, Up to 368 x 8 bytes of Data Memory (RAM)
Pinout compatible to the PIC16LF74
Pinout compatible to the PIC16LF74
Interrupt capability (up to 12 sources)
Eight level deep hardware stack
Direct, Indirect and Relative Addressing modes
Brown-out detection circuitry for
Parallel Slave Port (PSP), 8-bits wide with Universal Synchronous Asynchronous Receiver 8-bit, up to 8-channel Analog-to-Digital converter
Synchronous Serial Port (SSP) with SPI (Master
Timer2: 8-bit timer/counter with 8-bit period
Timer0: 8-bit timer/counter with 8-bit prescaler
Timer1: 16-bit timer/counter with prescaler,
Programmable memory protection
Power saving SLEEP mode
Selectable oscillator options before Break IC
In-Circuit Serial Programming (ICSP) via two
Watchdog Timer (WDT) with its own on-chip RC
Power-on Reset (POR)
Power-up Timer (PWRT) and Processor read access to program memory Oscillator Start-up Timer (OST) oscillator for reliable operation pins can be incremented during SLEEP via external crystal/clock register, prescaler and postscaler
Two Capture, Compare, PWM modules
– Capture is 16-bit, max. resolution is 12.5 ns
– Compare is 16-bit, max. resolution is 200 ns
– PWM max. resolution is 10-bit mode) and I2C (Slave) Transmitter (USART/SCI) external RD, WR and CS controls (40/44-pin only) Brown-out Reset (BOR)
Low power, high speed CMOS FLASH technology
Fully static design
Wide operating voltage range: 2.0V to 5.5V
High Sink/Source Current: 25 mA
Industrial temperature range
Low power consumption:
– < 2 mA typical @ 5V, 4 MHz
– 20 µA typical @ 3V, 32 kHz
– < 1 µA typical standby current
 Reverse Microchip MCU PIC16F77 Flash
Reverse Microchip MCU PIC16F77 Flash
Reverse Microchip MCU PIC16F77 Flash memory and locate the fuse bit of microcontroller, and extract code from MCU PIC16F777;
- High performance RISC CPU
- Only 35 single word instructions to learn
- All single cycle instructions except for program branches which are two-cycle
- Operating speed: DC – 20 MHz clock input DC – 200 ns instruction cycle
- Up to 8K x 14 words of FLASH Program Memory, Up to 368 x 8 bytes of Data Memory (RAM)
- Pinout compatible to the PIC16C73B/74B/76/77
- Pinout compatible to the PIC16F873/874/876/877
- Interrupt capability (up to 12 sources)
- Eight level deep hardware stack
- Direct, Indirect and Relative Addressing modes
- Brown-out detection circuitry for
- Parallel Slave Port (PSP), 8-bits wide with
- Universal Synchronous Asynchronous Receiver
- 8-bit, up to 8-channel Analog-to-Digital converter
- Synchronous Serial Port (SSP) with SPI (Master
- Timer2: 8-bit timer/counter with 8-bit period
- Timer0: 8-bit timer/counter with 8-bit prescaler
- Timer1: 16-bit timer/counter with prescaler,
- Programmable code protection
- Power saving SLEEP mode
- Selectable oscillator options
- In-Circuit Serial Programming (ICSP) via two
- Watchdog Timer (WDT) with its own on-chip RCProcessor read access to program memory
- Power-on Reset (POR)
- Power-up Timer (PWRT) and
- Timer2: 8-bit timer/counter with 8-bit period
- Universal Synchronous Asynchronous Receiver
- Parallel Slave Port (PSP), 8-bits wide with
- Brown-out detection circuitry for
Oscillator Start-up Timer (OST) oscillator for reliable operation pins can be incremented during SLEEP via external crystal/clock register, prescaler and postscaler after breaking Microchip mcu pic12f509 eeprom.
- Two Capture, Compare, PWM modules
– Capture is 16-bit, max. resolution is 12.5 ns
– Compare is 16-bit, max. resolution is 200 ns
– PWM max. resolution is 10-bit mode) and I2C (Slave) Transmitter (USART/SCI) external RD, WR and CS controls (40/44-pin only) Brown-out Reset (BOR).