 Break MCU Firmware
Break MCU Firmware
Non-invasive Break MCU Firmware are particularly dangerous in some applications for two reasons. Firstly, the owner of the device might not notice that the secret keys or data have been stolen, therefore it is unlikely that the validity of the compromised keys will be revoked before they are abused.
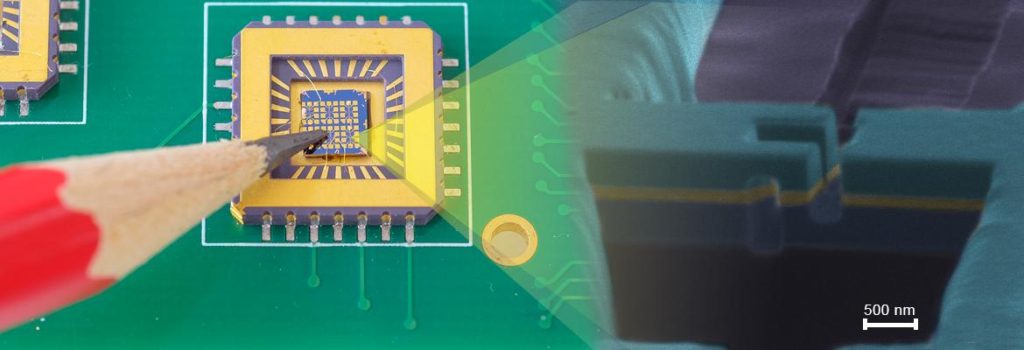
Secondly, non-invasive Microcontroller unlocking often scale well, as the necessary equipment can usually be reproduced and updated at low cost.
The design of most non-invasive ic cracks requires detailed knowledge of both the processor and software. On the other hand, invasive microprobing MCU reading require very little initial knowledge and usually work with a similar set of techniques on a wide range of products.
Attacks therefore often start with invasive reverse engineering, the results of which then help to develop cheaper and faster non-invasive attacks. Semi-invasive IC flash breaking can be used to learn the device functionality and test its security circuits. As these mcu cracks do not require establishing any physical contact to the internal chip layers, expensive equipment such as laser cutters and FIB machines are not required. The mcu firmware breaker could succeed using a simple off-the-shelf microscope with a photoflash or laser pointer attached to it.