 Restore IC Flash
Restore IC Flash
Restore IC Flash memory content after disable the security fuse bit, crack Microcontroller protection and extract the code from MCU memory;
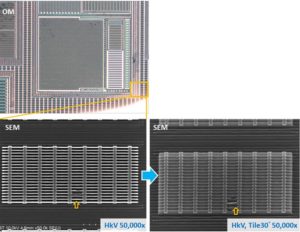
Restore IC Flash memory content after disable the security fuse bit, crack Microcontroller protection and extract the code from MCU memory
A non-invasive IC Flash Restore does not require any initial preparations of the device under test. The ic attacker can either tap the wires to the device, or plug it into a test circuit for the analysis. Once found, these ic breaks could be easily scaled and their reproduction does not involve very much cost. In addition, no tamper evidence is left after they are applied. Therefore they are considered to be the most serious threat to the hardware security of any device. At the same time it usually takes a lot of time and effort to find an ic copy on any particular device. This often involves reverse engineering the device in the sense of either disassembling its software or understanding its hardware layout.