 Extract MCU Firmware
Extract MCU Firmware
Extract MCU Firmware from program memory and data memory after remove the tamper resistance system of microcontroller and replicate the code to new MCU;
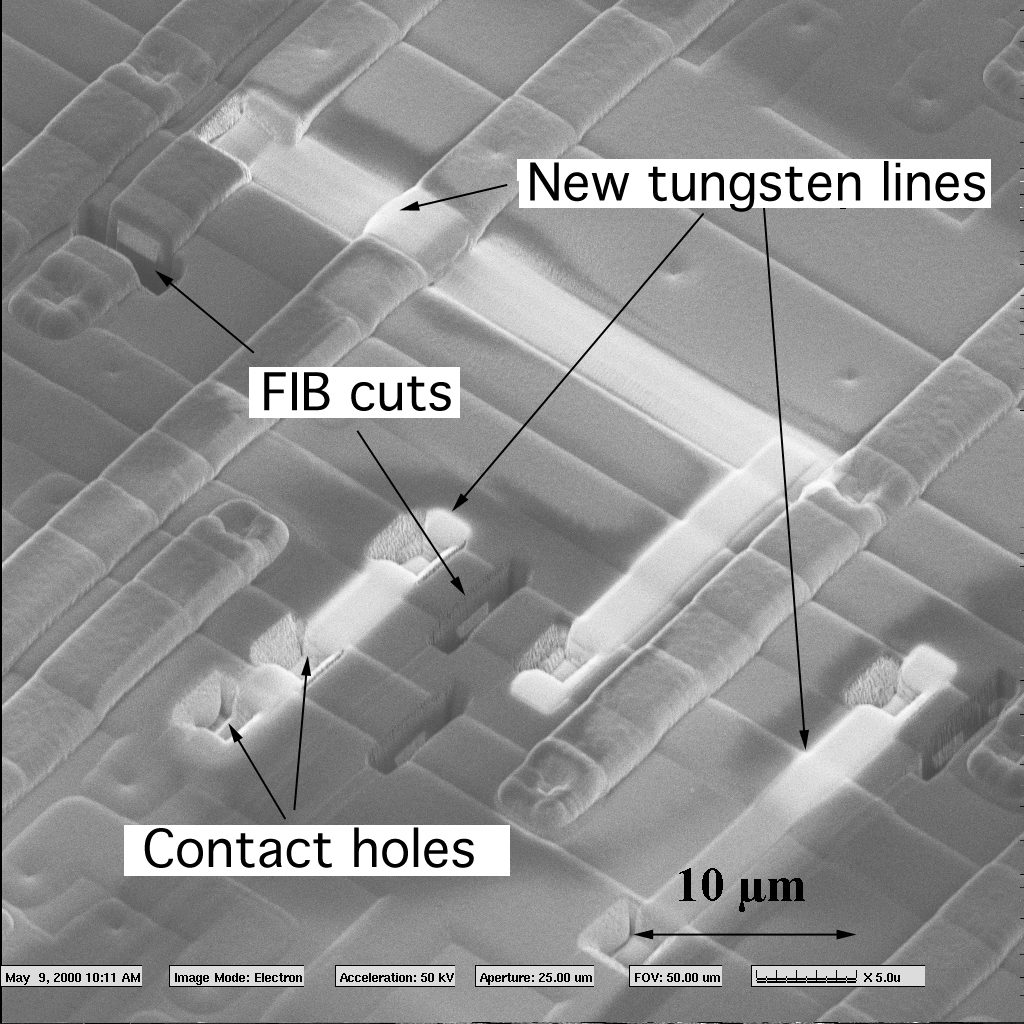
Some manufacturers intentionally do not provide any programming specifications for their MCU microcontrollers. That does not give very good protection on its own, and only slightly increases the cost of microcontroller reverse engineering, because this MCU firmware can be extracted by observing the signals applied to the IC chip during programming in a development kit or in a universal programmer.
Obviously, for the highest security, the system would not have any programming interface at all, and would not provide any access to stored data. This is normally the case for Mask ROM microcontrollers and smartcards. The only practical ways of attack chip flash in this case would be either to microprobe the data bus to recover the information or use power analysis and glitch attacks to exploit any vulnerability in software.
Relatively high security can be obtained when a microcontroller is user programmable but does not provide any read-back facility – only verify and write check, for example in the NEC 78K0S family Flash microcontrollers.
Of course this should be implemented properly to avoid the situation where the microprocessor decryption can force the system to verify one byte at a time. In this case he would need on average 128 attempts per byte (28 × 0.5) and assuming the byte access cycle is 5 ms it will take him less than a day to extract the contents of the memory, which is usually between 4 Kb and 64 Kb. Even if the verify operation is applied to large blocks of data, the mcu firmware extraction could try glitch attacks to reduce the cycle to a single byte.